How to set up a firewall
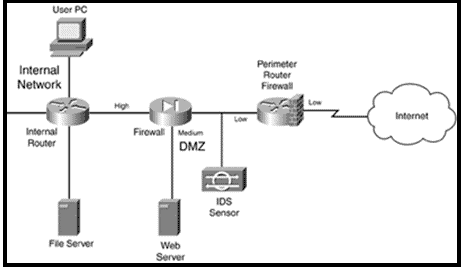
Setting up a firewall is crucial for securing your computer or network by controlling incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between your internal network and the internet, monitoring and filtering data packets to prevent unauthorized access and potential cyber threats. This comprehensive guide will walk you through the steps to set up and configure a firewall on both Windows and macOS systems, covering basic firewall concepts, types of firewalls, software and hardware options, and best practices for optimal security.
Understanding Firewalls
What is a Firewall?
- Definition: A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- Purpose: Protects against unauthorized access, malware, and other cyber threats by filtering data packets.
Types of Firewalls
- Software Firewalls:
- Installed on individual computers or devices.
- Examples: Windows Firewall (built-in), macOS Firewall (built-in), third-party firewall software.
- Hardware Firewalls:
- Dedicated devices or appliances placed between a local network and the internet.
- Provides centralized network security.
- Examples: Router with firewall capabilities, enterprise-grade firewall appliances.
Firewall Functionality
- Packet Filtering: Examines data packets and blocks or allows them based on predefined rules (IP addresses, ports, protocols).
- Stateful Inspection: Tracks the state of active connections to filter packets based on context (e.g., only allowing response packets to outgoing requests).
- Application Layer Filtering: Analyzes data at the application layer to enforce security policies based on application protocols (e.g., HTTP, FTP).
How to Set Up a Firewall: Step-by-Step Guide
Step 1: Determine Firewall Requirements
- Assess Network Environment:
- Identify network topology, devices, and potential security risks.
- Determine if you need a software firewall, hardware firewall, or both.
Step 2: Choose Firewall Software or Device
- Software Firewall (Windows):
- Windows Firewall: Built-in firewall in Windows operating systems.
- Third-Party Software: Install reputable firewall software (e.g., Norton Firewall, ZoneAlarm) for additional features and control.
- Hardware Firewall:
- Router with Firewall: Many routers offer built-in firewall capabilities.
- Dedicated Firewall Appliances: For enterprise environments, choose from various firewall appliances based on performance and feature requirements.
Step 3: Configure Software Firewall on Windows
- Access Windows Firewall Settings:
- Open Control Panel: Go to Control Panel > System and Security > Windows Defender Firewall.
- Windows Settings: Go to Settings > Update & Security > Windows Security > Firewall & network protection.
- Set Firewall Rules:
- Inbound Rules: Define rules to control incoming traffic.
- Outbound Rules: Define rules to control outgoing traffic.
- Customize Firewall Profiles:
- Domain, Private, Public Networks: Adjust firewall settings based on network location types.
Step 4: Configure Firewall on macOS
- Access macOS Firewall Settings:
- System Preferences: Go to Apple menu > System Preferences > Security & Privacy > Firewall.
- Enable Firewall:
- Turn on Firewall: Click on the lock icon to make changes, then click “Turn On Firewall.”
- Set Firewall Options:
- Allow Apps: Customize settings to allow specific apps to receive incoming connections.
- Stealth Mode: Prevents the computer from responding to probing requests.
Step 5: Define Firewall Rules
- Create Firewall Rules:
- Port-Based Rules: Specify allowed or blocked ports (e.g., allow TCP port 80 for web traffic).
- IP-Based Rules: Allow or block traffic from specific IP addresses or ranges.
- Protocol-Based Rules: Define rules based on network protocols (e.g., allow FTP, deny Telnet).
Step 6: Monitor and Manage Firewall
- Monitor Firewall Logs:
- Review firewall logs to track allowed and blocked connections.
- Identify potential security incidents or unauthorized access attempts.
- Update Firewall Rules:
- Regularly review and update firewall rules based on network changes and security requirements.
- Ensure rules align with organizational policies and compliance standards.
Step 7: Test Firewall Effectiveness
- Perform Security Tests:
- Use online tools or security software to perform port scanning and vulnerability assessments.
- Verify that firewall rules are effectively blocking unauthorized access and protecting network resources.
Step 8: Implement Additional Security Measures
- Use Intrusion Detection/Prevention Systems (IDS/IPS):
- Supplement firewall protection with IDS/IPS to detect and block malicious activities.
- Deploy VPN (Virtual Private Network):
- Secure remote access to your network by using VPN to encrypt traffic and bypass firewall restrictions.
Best Practices for Firewall Configuration
- Enable Automatic Updates: Keep firewall software and firmware up to date to protect against emerging threats.
- Use Strong Passwords: Secure firewall administrative interfaces and accounts with strong, unique passwords.
- Regular Audits: Conduct regular security audits and penetration testing to evaluate firewall effectiveness and identify vulnerabilities.
- Educate Users: Train users on safe computing practices and the importance of firewall security in preventing cyber attacks.
Conclusion
Setting up a firewall is a critical step in protecting your computer or network from unauthorized access, malware, and other cyber threats. By following the steps outlined in this guide for both Windows and macOS systems, you can effectively configure a firewall to monitor and control network traffic according to your security policies. Regularly monitor firewall logs, update rules as needed, and implement additional security measures to enhance network protection. If unsure about firewall configuration or encountering technical issues, consult manufacturer documentation, seek assistance from IT professionals, or refer to online resources for additional guidance.






